Captive Portal
Gartner Given Terms
Gartner Magic Quadrant
It provides a visual representation of different types of technology providers and their position in fast-growing markets.
SASE(Secure Access Service Edge)
- All users in branch office, home, roaming(airport) if he want to access any of cloud service() he will go thru SASE.
- Examples: Juniper Secure Edge, ZScaler Zero Trust SASE, Cisco Umbrella
- Example
- With SASE, security and all services delivered from cloud, allowing employees to securely connect to the corporate network and cloud applications from any location using a unified and consistent security policy
| N/W Without SASE | N/W With SASE |
|---|---|
|
Challenges: How can change my Network when? - More users are moving out of office(WFH, Roaming, BYOD(bring your own device)) - Companies have central HQ, where branch offices connect via WAN, home users via VPN(but also connecting to cloud directly) - How to do authentication, authorization
@startuml
skinparam componentStyle rectangle
rectangle "Branch Ofc" as bo {
actor "emp" as emp
actor "BYOD \nbring your\nown device" as byod
}
rectangle "head ofc" as ho {
[VPN] as vpn
[SSL] as ssl
[DLP] as dlp
[IPS] as ips
[LB] as lb
lb -u- ssl
}
actor "Mobile(Airport) \nRoaming User" as ru
[Cloud Services \n\n Salesforce,Office365\nApplications] as cloud
note right of ho
Hosts Stack of security appliances:
- protect users from internet
end note
ru -u- lb: VPN
byod -u- lb: VPN
emp -u- lb: VPN
ho -u- cloud
@enduml
|
Solving the Challenges - All security policies are applied, a single n/w stack is provided Benefits - Uplevel my security - Simplify my N/w(as devices for VPN,LB,FW,SSL,DLP,IPS sitting in HQ) can be removed - Branch office to HQ WAN not needed this Saves Million of $
@startuml
skinparam componentStyle rectangle
[Netskope client] as nsc #pink
rectangle "Branch Ofc" as bo {
[Netskope client1] as nsc1 #pink
[Netskope client2] as nsc2 #pink
actor "emp1" as e1
actor "emp2" as e2
e1 -u- nsc1
e2 -u- nsc2
}
actor "Bob\n(Airport) Roaming" as bob #red
[\t\tAWS \n\n Applications, Data] as aws
[\t\tAzure \n\n Applications, Data] as azure
[\t\tGCP \n\n Applications, Data] as gcp
cloud {
[internet]
}
cloud {
[internet2]
}
cloud {
[internet3]
}
cloud {
[internet4]
}
rectangle "SASE(Service on Cloud) = Netskope One Cloud" as r {
[Center (US)] as center
rectangle "PointofPresence \n\n POP1 (Virginia) \n Services:FaaS, AuuS" as pop1 {
[DLP] as dlp
[ZTNA] as ztna
[SWG] as swg
[CASB] as casb
}
[POP2 (Europe)] as pop2
}
rectangle "Okta(Auth Provider)" as ok
skinparam databaseBackgroundColor Aqua
database "Active Directory(Identity Provider)" as ad
center -- pop1
center -- pop2
internet -r- ad
center -r- internet : Authentication
internet -d- ok
swg -- internet2
internet2 -- nsc
nsc -- bob
nsc1 -u- internet4
nsc2 -u- internet4
internet4 -u- casb
center -up- internet3 : services
internet3 -u- aws
internet3 -u- azure
internet3 -u- gcp
@enduml
|
SD-WAN (Software-Defined Wide Area Network)
- Helps organizations to connect branch offices, central office(HQ), Services on cloud in fast, cost effective way
- Uses SDN(software defined network) to separate hardware and control mechanisms.
- Consider a retail chain(Relaince) with numerous branch offices across the country.
- Each branch office(store) requires reliable connectivity to Central or HQ services(eg: DB) to POS devices.
- 1 solution is to use MPLS for connectivity between stores and headquarters(But this is expensive), other is SD-WAN.
- With SD-WAN retail chain achieves cost savings, improved application performance
SSE (Secure Service Edge)
- Consider a healthcare organization(Apollo) that needs to provide secure access to electronic health records (EHR).
- Organization implements secure web gateways (SWG), next-generation firewalls (NGFW), intrusion prevention systems(IPS) into the network edge.
- Allows organization to enforce consistent security policies, inspect and filter internet traffic, and detect and mitigate threats in real-time
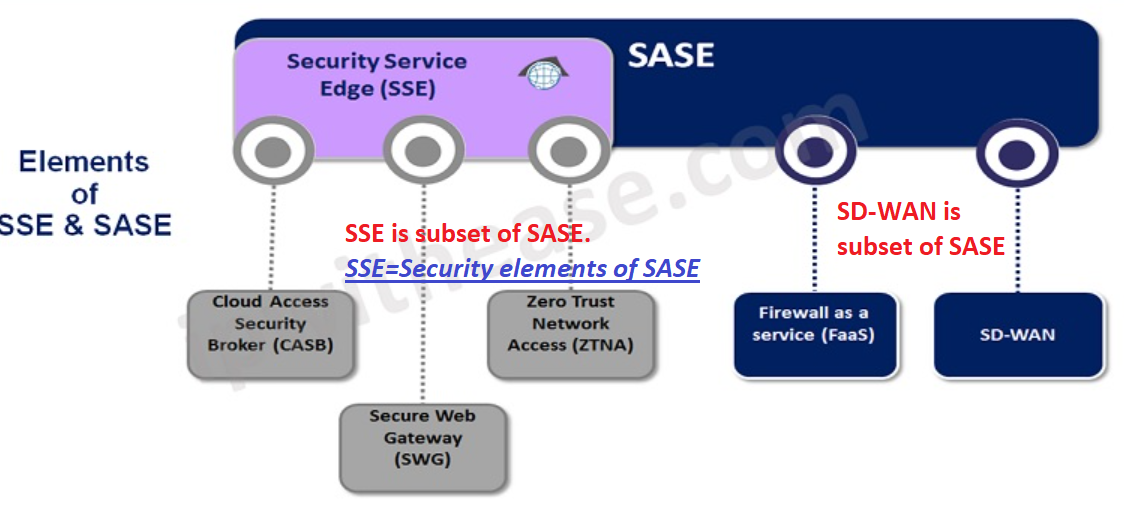
CASB, SWG, SASE
| CASB(Cloud Access Security Broker) | SWG(Secure Web Gateway) | SASE | |
|---|---|---|---|
| Subset of SASE | Yes | Yes | |
| Purpose | Protects applications sitting on cloud (SaaS, IaaS, PaaS) |
Protects web traffic going to cloud to access applications |
Networking, Cloud services converged under 1 umbrella |
| Features | DLP, Access Control | SSL Inspection, Malware Detection | SWG, SD-WAN, ZTNA, CASB |
| Deployment | Cloud based(mostly) | Cloud & onprem | cloud based |
| Use Cases |
Protecting data in cloud applications Compliance with regulatory requirements |
Securing web browsing for employees Blocking malicious web content |
Security information and event management(SIEM)
It can detect user behavior anomalies(Eg: from Active Directory event logs).
(Early Days) SIEM platforms were log management tools, They enabled real-time monitoring and analysis of security-related events.
(Present Day) SIEM software has evolved to incorporate user and entity behavior analytics (UEBA) & other advanced AI methods to identify anomalous behaviors and indicators of advanced threats.
2. Consolidate and sort to identify threats and adhere to data compliance requirements.
- Incident monitoring and security alerts
- Open Source SIEM Solutions
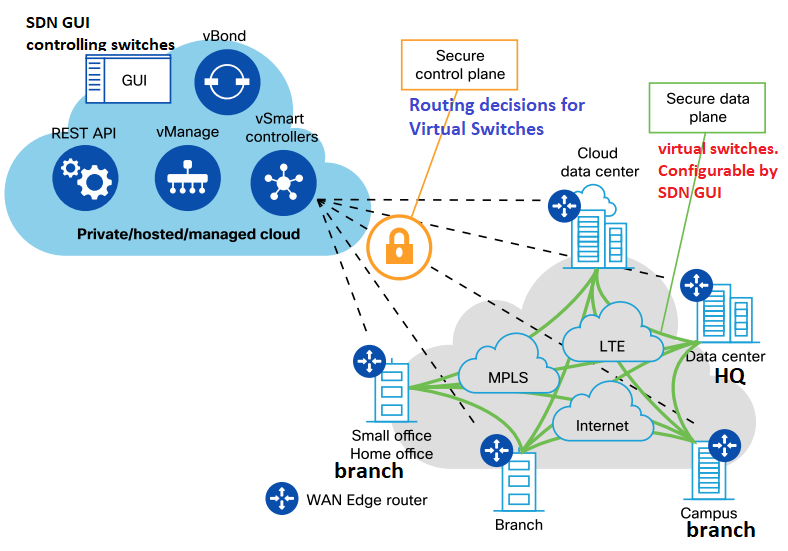
Software Defined Networking
Forwarding Plane(lies on Switch), Control Plane(lies on GUI).
Controlling switches routing decisions from GUI. Person does not have to go physically to control/change Switch/Router.
@startuml
skinparam componentStyle rectangle
[GUI1] as gui1
[GUI2] as gui2
[SDN App1] as app1
[SDN App2] as app2
[SDN-Controller-Server(Control Plane)] as con
[switch-chip1(Data Plane)] as sc1
[switch-chip2(Data Plane)] as sc2
[switch-chip3(Data Plane)] as sc3
gui1 <--> app1
gui2 <--> app2
app1 <--> con
app2 <--> con
con <--> sc1
con <--> sc2
con <--> sc3
@enduml